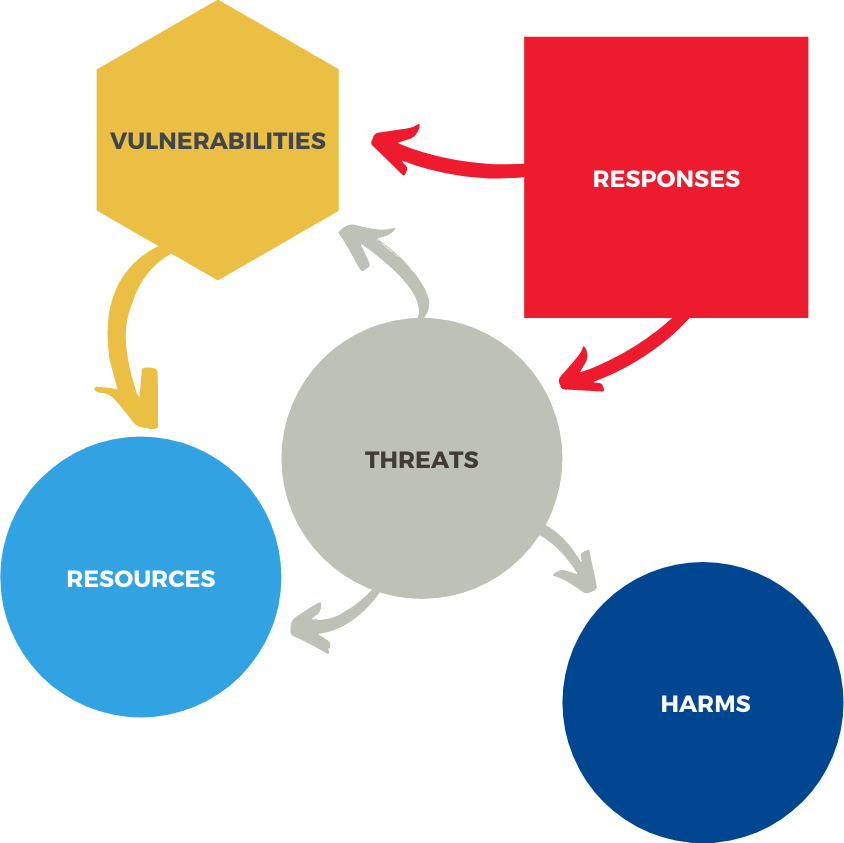
The Smart Citizen Cyber Resilience Ontology (SC2RO) maps the cyber resilience landscape for individuals. It identifies cyber resources, vulnerabilities, threats, responses and harms associated with and specific to individual citizen’s cyber functionings.
Cyber resilience is the ability to maintain positive functioning and adaptation in the context of adverse cyber incidents, which can be technical, socio-technical, natural, and man-made.
Resources in this ontology are framed much broader than what is typically referred to as Assets, and they include physical resources - such as computing devices, digital resources - such as data and software, as well as individual resources - such as personal endowments, identity, and social capital. Resources enable individuals to achieve specific cyber functionings.
Vulnerabilities are weaknesses in Resources that can be exploited by Threats. The ontology currently identifies three types of vulnerabilities: individual, physical, and digital. Individual vulnerabilities are situations and attributes of individuals that not only expose them to threats but also that can be exploited and compromised by specific threats. Physical vulnerabilities are weaknesses associated with the materiality of cyber resources. Digital vulnerabilities are weaknesses associated with software, data and networking / connectivity resources.
Threats are potential adverse incidents and “unfreedoms” that limit individuals’ cyber capabilities and functionings. The framing of these in the ontology is informed by the personal, social, and environmental conversion factors that constitute individuals’ personal utilization function.
Responses, which are also called Countermeasures, are framed around the four resilience phases of prepare, absorb, recover, and adapt. The Prepare phase is the nominal baseline cyber functioning of individuals. The Absorb phase is triggered by the onset of an adverse cyber incident to limit the immediate impact of the adversity. The Recover phase is towards restoration of lost cyber functioning. The Adapt phase is the positive adaptation from the cyber incident through evolution and enhanced cyber functioning.
Harms are the realized impacts of the unmitigated threats whose ultimate effect on individuals is to reduce their cyber capabilities and hamper their cyber functionings.
For more details you can browse the documentation or view the visualization of the ontology. Alternative versions of the documentation are available here and here.
Why is this important?
Cyber resilience has largely been framed from the perspectives of nation-states, governments, and the private sector. This framing tends to neglect the cyber resilience role of civil society stakeholders. Further, cybersecurity frameworks, as well as resilience management frameworks have focused on building the security and resilience of critical infrastructures, information systems, critical sectors, and for-profit organizations.
Such a focus makes it difficult to operationalize cyber resilience into relevant instruments and modalities for engagement and participation of civil society stakeholders as active cyber resilience agents.
What is the big idea?
This ontology is part of a project that aims to enhance the resilience of citizens in smart digital futures.
Digital technologies are part and parcel of our daily lives, as individuals, communities, cities, countries, and the global community. They provide numerous benefits that improve our overall quality of life. However, there are also significant adverse impacts that are cause by and enabled by digital technologies. The goal of cyber resilience is for life to continue and for people to thrive despite these significant adverse impacts.
Why an ontology?
Ontologies provide a superior knowledge formalization that allows for semantic processing and reasoning about data.
The SC2RO ontology can be used for several purposes including:
- To provide a common vocabulary and shared understanding of the citizens’ cybersecurity domain
- To facilitate semantic interoperability, communication, and coordination between stakeholders (e.g., for incident reporting)
- To serve as a reference model and to inform operationalization of citizens’ cyber resilience
- To serve as a knowledge repository for relevant ICT artifacts and tools (e.g., risk assessment tools, APIs)
How can you get involved?
You can contribute towards this goal by:
- Refining the concepts in the ontology
- Suggesting and motivating for updates in the structure of the ontology
- Suggestig updates to the definition of the concepts
- Providing robust examples of countermeasures / responses that work for specific cyber threats
- Building tools and applications that make use of the ontology
- Contributing in any other way towards enhancing our global cyber resilience